Paper Password Splitting
 What will happen to your password-protected accounts upon your death? Will people you trust be able to access them? Do you feel unsafe writing your passwords down?
What will happen to your password-protected accounts upon your death? Will people you trust be able to access them? Do you feel unsafe writing your passwords down?
This is probably a somewhat uncomfortable topic, but one that deserves some attention. It turns out that we can solve this problem by "splitting" passwords on paper. This article will show you how to do it. No fancy software is needed, the instructions are simple enough to be included in your will, and it doesn't cost anything.
Recovery
If you’re here to recover a passphrase, this article will introduce you to the process. More information and wordlists are available here.
Contents
- Introduction
- Split into 2-of-2 Recovery Passphrases
- Split into 2-of-3 Recovery Passphrases
- Select Safe People or Places
- Fill Out Recovery Sheets
- Test Instructions
- Distribute the Recovery Phrase Sheets
- Annual Maintenance
- Non-Diceware Password Splitting
Introduction
What's Password Splitting?
Here's a simplified example — say this is our password (or "passphrase"):
delirious broaden sheep
We can "split" this passphrase into two "recovery phrases" and write them on separate sheets of paper. This one is left in a safe deposit box at a bank:
quickness exert july
and this one is kept in a fireproof safe:
overrate sleep establish
As you can see, the two recovery phrases above look random. One actually is random, and the other is indistinguishable from a random phrase. Neither one reveals anything about the original passphrase. With the method described in this article, if both recovery phrases are combined, the original passphrase can be recovered.
Which Passwords Should be Split?
Your financial accounts, and other property, will be bequeathed to your beneficiaries according to your designations and according to your will. It’s essential to have this all in place and verified from time to time, so take care of this if you haven’t already.
However, you probably have some valuable password-protected accounts or other property that won’t be accessible by your beneficiaries. Examples include valuable family photos and email records accessible only with
- smartphone passcodes, or
- computer passwords, or
- Internet accounts.
These are the types of passwords we’re concerned with in this article.
Okay. So you’d like a select few trusted people to have access to some password-protected accounts once you can no longer access them yourself. And you don’t want to just write your passwords down on paper. Let’s solve this problem.
This method does not involve any fancy software or even a computer — split passwords can be recovered with a pen and paper.
Before we begin, note that Diceware™ is a trademark of Arnold G. Reinhold, and for more information you can visit his Diceware page.
Select a Password and Wordlist
If you have more than one password you'd like to secure with paper password splitting, it's easiest to put the passwords into a password manager (LastPass, KeePass, 1Password, or similar) then secure the password manager with a single master passphrase. See the Diceware article for how to create a strong master passphrase — that master passphrase is the password we'll split. Note that if a password manager offers password recovery, that defeats the purpose of securely splitting its master passphrase on paper. Don't choose a password manager that offers master password recovery.
If you have an individual passphrase you'd like to split, all the words in the phrase must appear in a numbered wordlist with both regular numbers and dice roll numbers. If they don't, you'll either have to treat it like a regular password (see "If you have a regular password" below) or change to a new passphrase. For a numbered wordlist, I recommend you use my 2019 Diceware wordlist here, which looks like this:
number dice word
...
5030 46252 puzzle
5031 46253 puzzling
5032 46254 pyramid
5033 46255 python
5034 46256 quack
...
You could split a regular password, but you'll have to do more translating between characters and numbers than if you split a passphrase. Pick a numbered ASCII character list (this or this) and then in following along with this article, when a whole passphrase word is translated to or from a number, you will translate a single character from your password. See the Non-Diceware Password Splitting section for more details.
An ASCII character list looks like this:
number dice letter
...
27 153 or 432 a
28 154 or 433 b
29 155 or 434 c
30 156 or 435 d
31 161 or 436 e
...
Once you have your passphrase to split, we can begin.
Split Into 2-of-2 Recovery Passphrases
Have your wordlist handy. For this example, we're using my 2019 wordlist.
Let’s say we roll dice to make a random 3-word Diceware passphrase, and we’ll call it the secret S. We roll ⚁⚁⚄⚅⚀, ⚀⚃⚁⚂⚂, and ⚄⚃⚁⚀⚄
Secret S
1687 22561 delirious
699 14233 broaden
5873 54215 sheep
Using the line numbers from my 2019 wordlist, not the 5-digit dice numbers, we get
Secret S
delirious (1687) broaden (699) sheep (5873)
Note that a three-word passphrase is not strong, and it used for these examples only. Use at least seven words in your real Diceware passphrases.
To split S into two recovery phrases, both of which are needed to recover it (hence calling it "2-of-2"), we must roll dice again to create a new random 3-word passphrase that we’ll call recovery phrase A1. Say after rolling dice we have
Random Recovery Phrase A1
quickness (5054) exert (2414) july (3518)
Now for each word in S we’ll subtract the corresponding word in recovery phrase A1. If the result is not from 1-7776, we’ll add 7776 (this is called "subtracting modulo 7776"). Why 7776? Because that's the number of words in the wordlist we're using.
(S - A1) mod 7776
S: delirious (1687) broaden (699) sheep (5873)
A1: quickness (5054) exert (2414) july (3518)
delirious (1687) - quickness (5054)
1687 - 5054 → -3367 → -3367 + 7776 → overrate(4409)
(since -3367 is less than 1, we add 7776 to get a number from 1-7776)
broaden (699) - exert (2414)
699 - 2414 → -1715 → -1715 + 7776 → sleep (6061)
(since -1715 is less than 1, we add 7776 to get a number from 1-7776)
sheep (5873) - july (3518)
5873 - 3518 → establish (2355)
After subtracting the numeric values of the words we now have recovery phrase A2.
Recovery Phrase A2
overrate (4409) sleep (6061) establish (2355)
Recovery phrase A1 is completely random, and phrase A2 is indistinguishable from randomness on its own. But if we take both recovery phrases add them we recover the original secret S! When adding, we’ll subtract 7776 if any sum is larger than 7776:
(A1 + A2) mod 7776
A1: quickness (5054) exert (2414) july (3518)
A2: overrate (4409) sleep (6061) establish (2355)
quickness (5054) + overrate (4409)
5054 + 4409 → 9463 → 9463 - 7776 → delirious (1687)
(since 9463 is larger than 7776, we subtract 7776 to get a number from 1-7776)
exert (2414) + sleep (6061)
2414 + 6061 → 8475 → 8475 - 7776 → broaden (699)
(since 8475 is larger than 7776, we subtract 7776 to get a number from 1-7776)
july (3518) + establish (2355)
3518 + 2355 → sheep (5873)
After adding the recovery phrases A1 and A2, we have recovered S:
delirious broaden sheep
Let’s recap:
- we rolled dice to create secret
Sofdelirious broaden sheep - we rolled dice again to create recovery phrase
A1ofquickness exert july - we subtracted
A1fromSto get recovery phraseA2ofoverrate sleep establish - by adding
A1andA2, we recoveredS
We're back to the example at the beginning of this article. We see that we can write down quickness exert july on one piece of paper, and overrate sleep establish on another piece of paper. If we trust two people with those slips of paper, neither one of them has our secret passphrase. If we also give them instructions, those two people could re-create the secret passphrase S. That’s it! If you want more background information on this method, this is called encryption with a one-time pad.
Split Into 2-of-3 Recovery Passphrases
The above 2-of-2 method has a problem, though. If either of the above recovery phrases is lost, the secret passphrase can never be recovered! This doesn’t seem terribly reliable for safeguarding a secret for many years.
Let’s build upon our scheme to create a 2-of-3 system, where we create three pairs of recovery phrases. If any one of the three is lost, the secret passphrase can still be recovered with the remaining two recovery phrases. This is a more complex system, but it's more reliable.
To split a secret into three parts, any two of which can create the secret, we need to come up with three recovery phrases A1, B1, and C1, each of which is subtracted from the secret S to create phrases A2, B2, and C2.
From above, we have
Secret S
delirious (1687) broaden (699) sheep (5873)
Random Recovery Phrase A1
quickness (5054) exert (2414) july (3518)
Resulting Recovery Phrase A2
(S - A1) mod 7776
overrate (4409) sleep (6061) establish (2355)
Let’s roll dice again to create recovery phrase B1 then subtract to create B2
Random Recovery Phrase B1
anyplace (248) couch (1349) happiest (3132)
Resulting Recovery Phrase B2
(S - B1) mod 7776
croon (1439) undying (7126) frightful (2741)
One more time, let’s roll dice to create C1 then subtract to find C2
Random Recovery Phrase C1
outage (4305) malformed (3823) serpent (5823)
Resulting Recovery Phrase C2
(S - C1) mod 7776
rebuttal (5158) petunia (4652) activist (50)
Now we have three pairs of recovery phrases, where each pair recovers S:
(A1 + A2) mod 7776 → S
(B1 + B2) mod 7776 → S
(C1 + C2) mod 7776 → S
If you distribute those recovery phrases, like so, to three safe people or places:
A1 and B1 go to safe place or person 1
C1 and A2 go to safe place or person 2
B2 and C2 go to safe place or person 3
then any two safe places or people together have one pair of recovery phrases (A1 + A2) or (B1 + B2) or (C1 + C2).
This 2-of-3 method reduces the risk that your secret is lost forever. In the above example, say "safe place or person 2" loses phrases C1 and A2 a fire, then the secret S can still be recovered using (B1 + B2).
Next we'll discuss later exactly what a "safe place or person" is.
Select Safe People or Places
If you're using 2-of-2 splitting, you'll need to choose two different safe places or people to trust your paper recovery phrases to. And three if you're using 2-of-3 splitting.
Recommendations:
- Your filing cabinet along with your will or other valuable papers, or
- a fireproof safe, or
- trusted with a family member, or
- in a safe deposit box at your bank, or
- with your attorney or accountant.
If possible, it's recommended to choose people/locations in separate cities or at least separate buildings to minimize fire and other risks.
You can also choose to store one recovery phrase digitally (recommended only if using 2-of-3 splitting). The only recommended place at the time of writing is in a document in Google Drive. If your Google account goes inactive for some time (presumably after you've died or some other issue has arisen), Google can automatically provide access to your Google Drive to a designated person:
- Fill out two text file recovery sheets (see below) for two recovery phrases: (A1 and B1) or (C1 and A2) or (B2 and C2) as shown above.
- Save the recovery sheet text files to your Google Drive.
- Set up your personal Google account's Inactive Account Manager:
- provide access to your Google Drive to your designated person, and
- include instructions in the notification email to that person to "see my passphrase recovery documents in my Google Drive".
- Print and and fill out four paper recovery sheets for the remaining four recovery phrases
If you want to use the Google Drive as a digital "safe place," it's recommended that you only use it for 2-of-3 splitting, not for 2-of-2. If the person whom you trust changes their email addresses, or doesn't see the notification email, etc., the recovery phrases kept on Google Drive are effectively lost.
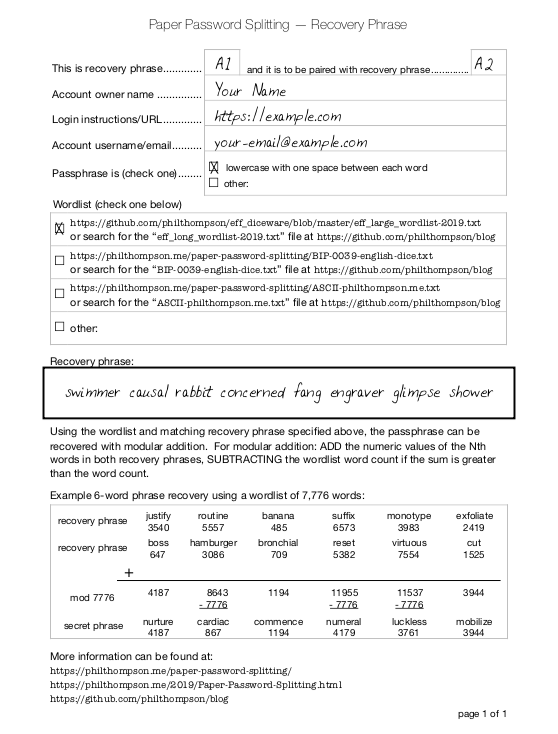
Fill Out Recovery Sheets
Each recovery phrase should include clear instructions in order for our password to actually be recovered. PDF sheets are available for printing. Print out one sheet per recovery passphrase and fill it out by hand. For digital recovery phrases there's a text file as well.
An example filled sheet is below:
Note that recovery sheets should NOT indicate where any other recovery phrase sheets are, or who has them. That knowledge is entrusted with the individuals you’ve selected.
Test Your Instructions
Double check that you've indicated the correct wordlist to use for recovery on all recovery sheets, and that each pair of recovery passphrases works as intended to recreate your secret passphrase.
Make sure everything needed to actually access the account is provided on the recovery sheet:
- Is two-factor authentication enabled on the account? If so, you'll want to include all relevant information so the account can be accessed, including perhaps the phone number if text messaging two-factor authentication is used, or if a "Google Authenticator"-style one-time codes are used, you could make a backup of the code and staple it to the recovery sheet.
- If the password is for KeePass or some other password-protected computer file, note where the file can be found and the names and versions of the software used to create and open the file. Perhaps the you'll want to leave the file on a USB drive or in a certain location on your computer's hard drive.
Distribute the Recovery Phrase Sheets
If you're using Google Drive with Google's Inactive Account Manager, you should have filled out two text file versions of the recovery sheet. Otherwise, at this point you should have your recovery sheets printed and filled out by hand: two sheets for 2-of-2 splitting, or six sheets for 2-of-3 splitting.
You can now provide your paper recovery sheets to your safe people/places.
Annual Maintenance
Create a calendar reminder. Every year, you’ll want to check a few things.
- Is your 15 year old seven-word Diceware passphrase now considered too short to be safe?
- Has your master passphrase changed? If so, you need to recreate new recovery passphrases and distribute them.
- Do all your designated people/places still have access to your recovery passphrase as intended?
- Was there a chance an unauthorized person saw one of more of your recovery phrase sheets during the year? If this is a possibility, you’d want to change your passphrase and distribute new recovery sheets.
Non-Diceware Password Splitting
Diceware allows us to pick strong purely random recovery phrases by rolling dice. It's also possible to use dice with other wordlists (and character lists) to create recovery phrases. The easiest way to do this is to use the custom-numbered wordlists below:
- 94-character numbered ASCII character list uses three 6-sided dice to select individual characters for a traditional password
- 2048-word BIP39 English Wordlist uses five 6-sided dice
For example, we can split a 12-character regular password with a 94-character numbered ASCII character list.
If our secret password S is
Password S
v1Bu5B@bzp\;
The number value for each character can be found in the 94-character numbered ASCII character list as
48 1 54 47 5 54 12 28 52 42 83 85
By rolling three 6-sided die, one roll per character in the passphrase, we can come up with recovery phrase A1
roll 431 → + (26)
roll 261 → O (67)
roll 312 → V (74)
roll 512 → y (51)
...
26 67 74 51 43 13 81 60 71 83 37 35
Recovery Password A1
+OVyq#{HS\ki
Then by subtracting A1 from S we find recovery password A2:
(S - A1) mod 94
48 1 54 47 5 54 12 28 52 42 83 85
- 26 67 74 51 43 13 81 60 71 83 37 35
----------------------------------------------------------
22 -66 -20 -4 -38 41 -69 -32 -19 -41 46 50
+94 +94 +94 +94 +94 +94 +94 +94
----------------------------------------------------------
22 28 74 90 56 41 25 62 75 53 46 50
~ b V . D o = J W A t x
Recovery Password A2
~bV.Do=JWAtx
For more background, here are some excellent resources I came across while researching this topic: